There are 2 tools to utilize search engine:
– the Harvester using the terminal
– Maltego
Using the Harvester through the terminal will only give you information that is leaked or available on the search engine. To use this tool is very easy, open the terminal on your kali linux, and type theharvester or theHarvester depends on your version of kali linux. -d is the domain that you want to search -l is the amount of data you want your terminal to show -b is the search engine you want to use.
For example: theHarvester -d facebook.com -l 100 -b bing
When you enter the command, it will show you the results it can find with a maximum amount of 100 results.
Another tool is using maltego. Maltego is an application that is available on kali linux. Before using this application, you must register yourself and log in to use the tools in maltego. After you log yourself in, you will see many tools that are available for you to use. But for finding data behind a website or a domain, you can just click new graph, and press what you want to find trace of, if you want to find information traces from a domain, you can choose domain, name the domain you want to find, and then click transform. Wait for a while until all the data are showed, it will be showed in the form of trees and branches. Something like this:
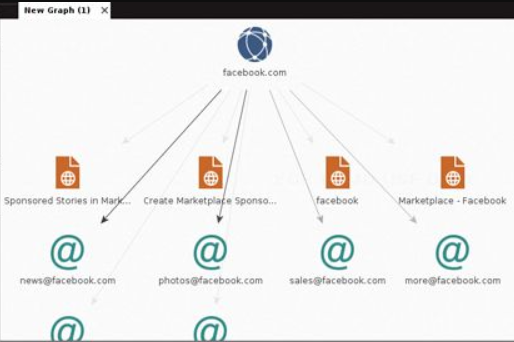
If you want to find a data about another person, you can! But you have to log in to your twitter first, after you are done with logging in to your twitter account, maltego will find the data related to the person you are searching for.
Category Archives: Ethical Hacking
Footprinting Tools
There are several footprinting tools available in kali linux, such as:
– Whois using the terminal
– Host command
– Samspade
– Greenwich
The purpose of footprinting tools is to gather data which is left exposed by the internet, information such as the owner of the domain, the server name, location address, email address could be exposed if the website is not secure enough to leave these prints. Some of these tools are not only available in kali linux, there are many website available for footprinting tools.
For example: using whois lookup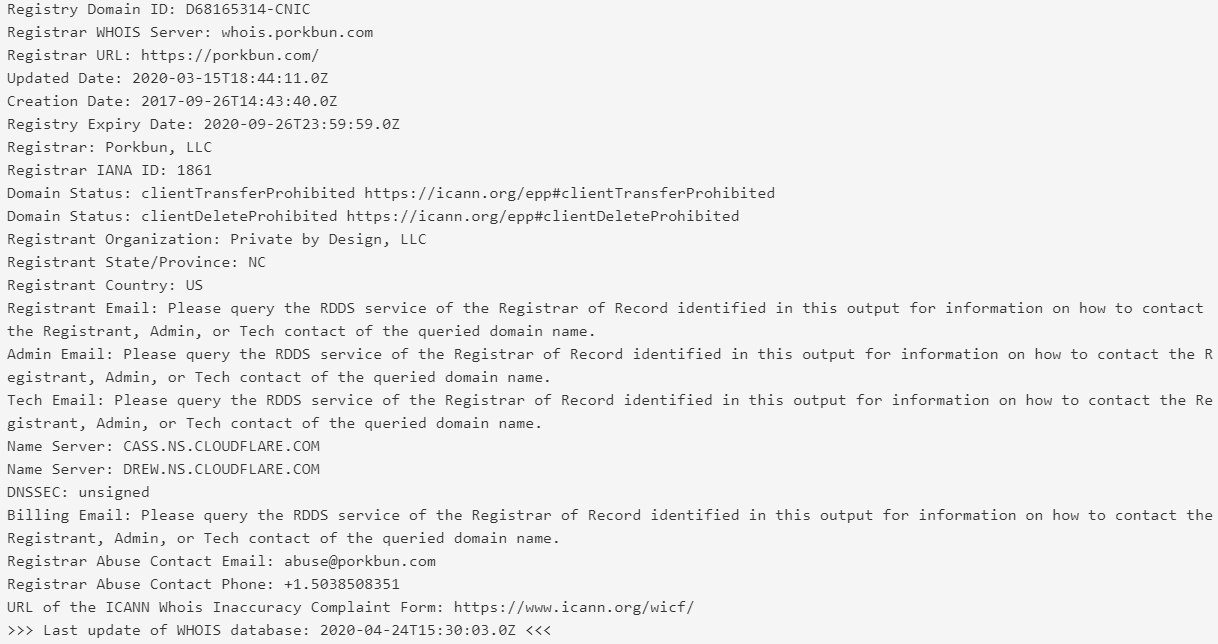
or using censys.io
Other than that, there is also a tool to track the DNS (Domain Name Sevice), such as:
– dnsenum
– dig
Meet In The Middle
Meet in the middle is a type of attack that will attack the network. When someone use this tool, they will be able to track the network traffic of their own computer or their local network, or any kind of network. This attack is dangerous due to the fact that it can intercept the traffic of the network. It means that, every data sent through the network can be tracked and be read by this, especially when logging in or signing up to a website.
One of the tools used for this attack is Burp Suite. Burp Suite is a tool that can intercept the network on your computer. In kali Linux, this tool is already available and ready to use.
When you already open the burp suite, click the proxy and turn on the intercept, and then click the option, which will show the default proxy listener which is 127.0.0.1:8000
Using the firefox in kali Linux, go to the preference and search for proxy, click the option and turn on manual proxy and write the default proxy listener that you see on your burp suite.
After you change the proxy into the manual one, try to go to any website. You will not be able to access the page, you need to download the certificate of burp suite since the proxy is not detected in any of the default certificate in the browser. To download the certificate, go to http://burp and you can see a little writing “CA Certificate”, when you click on that you can download the certificate. And then go to the browser again, go to the preference and search for certificate, then add your downloaded certificate there.
If you load the website you failed to access earlier, you will be able now. And if you go back to burp suite, it will show you your network traffic. You will have to be extremely careful when you enter your username and password, because the traffic can show the data and other people can see them!
If you notice, beside the search engine of the firefox, there will be a green lock, and you can view the certification there. It is not authorized so it will give a warning. And the name of the verified by will be different from the normal one. If you want to make it looks like it is a legitimate certification, you can make the certification by yourself and edit the name of the publisher and other thing.
